Blogs
Weekly Blogs For A Quick Informative Read!
The Pursuit of Anonymity: Strategies to Protect Your Online Identity
Being completely anonymous is nearly impossible, but you may greatly minimise what the internet...
Navigating the Cybersecurity Seas: A Guide for UK Startups in the Digital Age
A Guide for UK Startups in the Digital Age In today’s digital world, cybersecurity compliance...
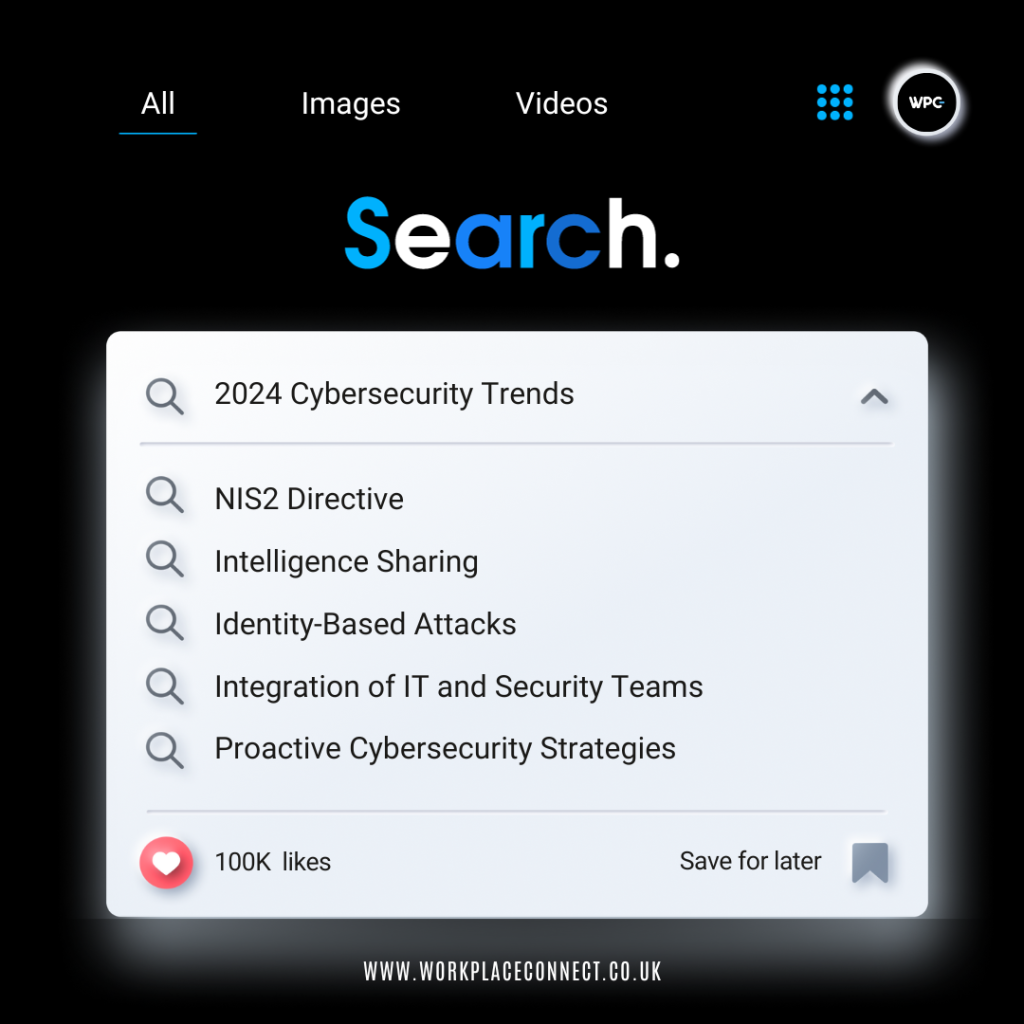
Navigating the Digital Frontier: Top 2024 Cybersecurity Trends
Cybersecurity is once more at a crossroads ahead of 2024, with a fast-expanding threat...
Ho-Ho-Hold Your Cyber Defences: A Holiday Guide to Online Safety
The holidays should be a joyous time for everyone, full of goodwill and harmony. Unfortunately,...
Cybersecurity Alert: Mega-Scale DDoS Attack Imperils Global Businesses – Highlights for the Month
The largest-ever DDoS Onslaught Affects Businesses Throughout the World Companies such as...
Securing the Digital Vaults: The Critical Role of Cybersecurity in Document Management
Untold amounts of sensitive data are stored in the vast number of documents that are amassed...
Data Privacy in a Hyperconnected World: Challenges and Solutions
Businesses rely largely on technologies based on data to develop and stay competitive....
Understanding DDoS Attacks: Mitigation and Prevention Strategies
What is a Denial-of-Service Attack? When authorised individuals are unable to gain access to...
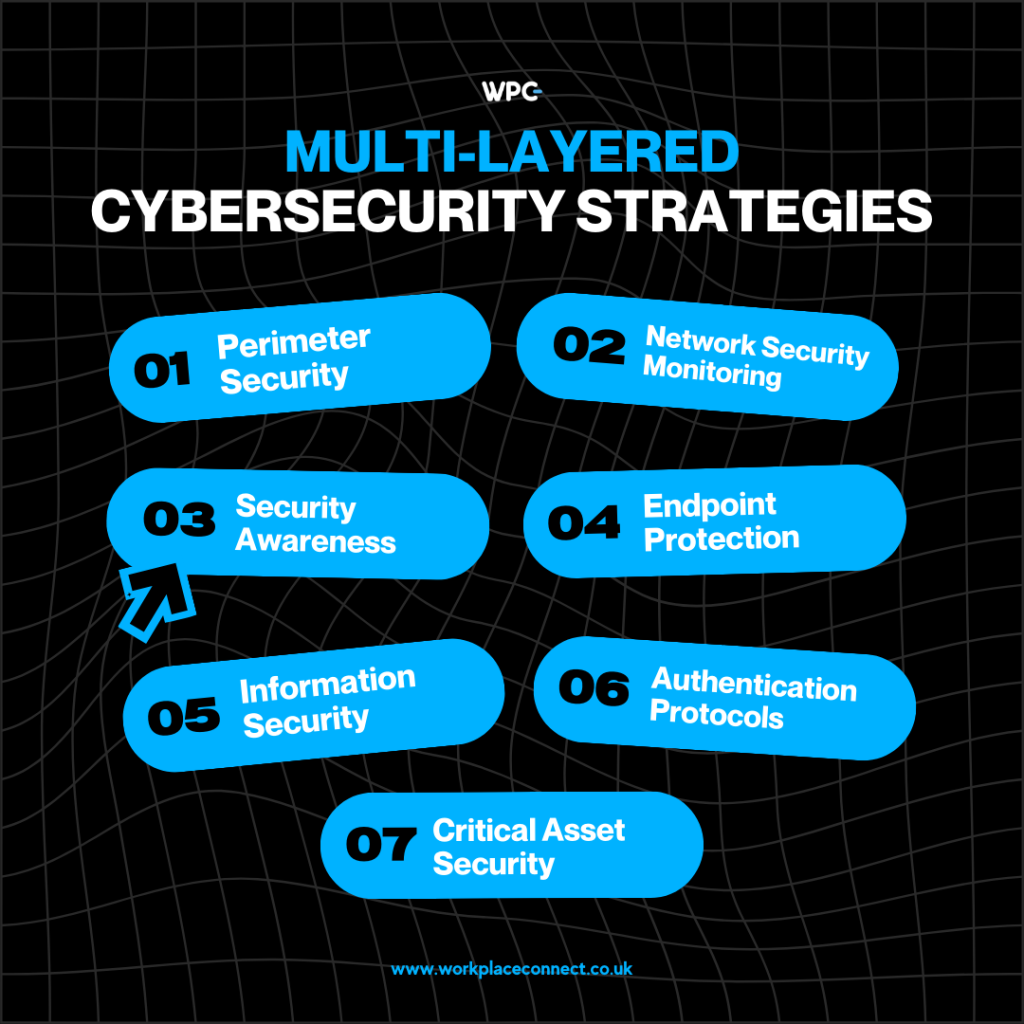
Raising the Shield: The Importance of Multi-Layered Cybersecurity Strategies
Cybersecurity dangers to enterprises grow year after year. Companies, however, can tackle new...
Our Accreditations