Blogs
Weekly Blogs For A Quick Informative Read!
Cybersecurity Audit Checklist: Ensuring Robust Protection for Your Organisation
Newer risks to security are constantly appearing, and as a result, legal requirements are...
Think Like A Hacker
Find your security flaws before hackers do While companies still utilise conventional defences...
Death By Cheapness
Costs associated with cyber security are rising. When you consider the dangerous landscape of...
Dangers of the Dark Web: Safeguarding Your Organisation
The dark web, often known as the darknet, is a section of the internet that is impossible to...
Disaster Recovery Planning: A Crucial Investment for Your Business’s Future
Disasters can occur at any time, endangering your confidential data and severely hurting your...
Ransomware 101: A Comprehensive Guide to Understanding and Protecting Yourself Against Ransomware Attacks
What is Ransomware? Malware called ransomware is made to prevent a user or business from...
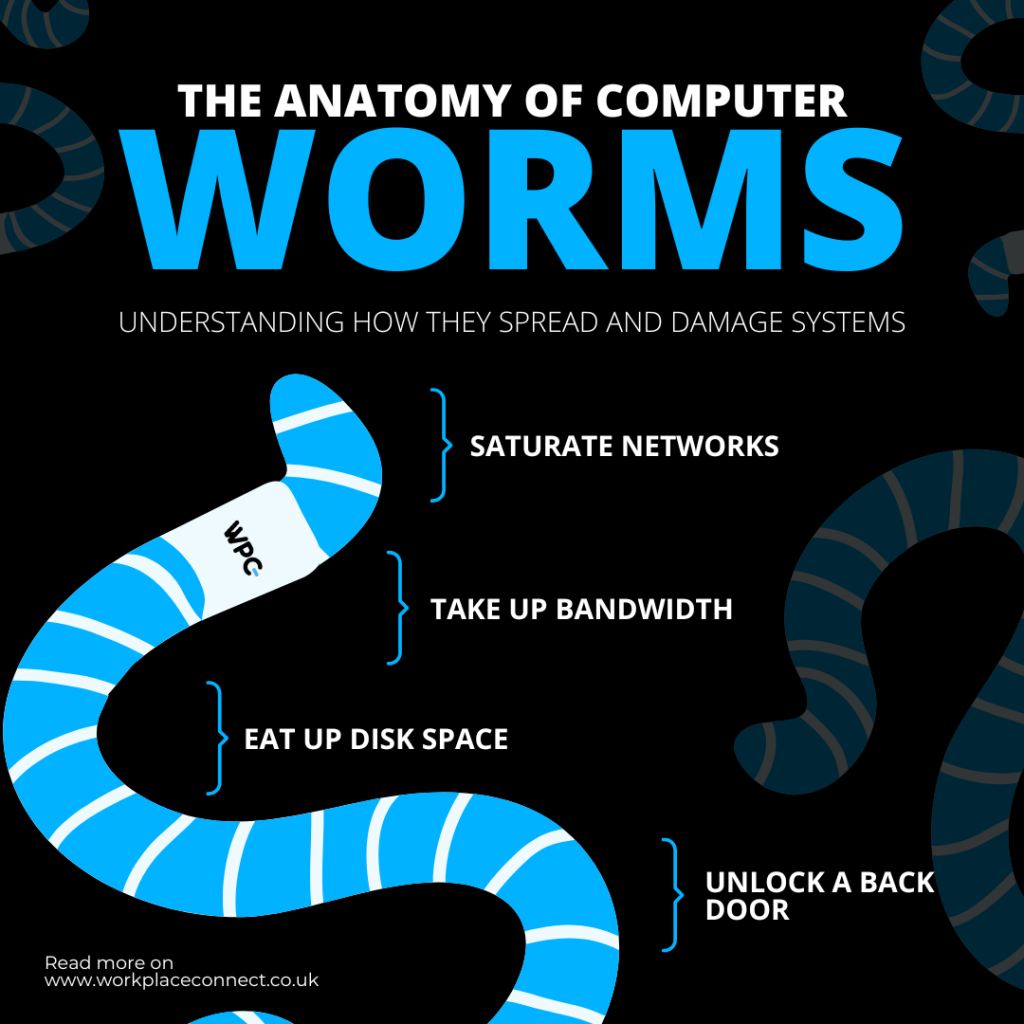
The Anatomy of Computer Worms: Understanding How They Spread and Damage Systems
Do you know what computer worms are? These harmful apps have the potential to compromise your...
Monitor Endpoints, Maximise Protection
Once upon a time, company IT environments were quite basic. They were made up of a few...
Protecting Yourself from the Risks of Public Wi-Fi: Essential Safety Tips
The Work-Remotely Movement is The New Normal An unparallelled year for cyberattacks happened in...
Our Accreditations