Blogs
Weekly Blogs For A Quick Informative Read!
Debunking Myths: Cybersecurity Edition
Companies may occasionally operate in ways that are inconsistent with reality when it comes to...
Boosting Your Company’s Mobile Device Security: Best Practices and Solutions
The times have changed, and so has the nature of sensitive information that can be accessed...
Cybersecurity Audits: What, How, and Why
One of the major mistakes companies make is expecting that routine risk assessments maintain...
Are You Unintentionally Wasting Money on IT?
Global IT investment is anticipated to hit £3.2 trillion this year, according to a report...
The Best Of The Best: A Guide to Choosing The MSP For You
Technology is constantly changing. While improvements in hardware, software, and networking can...
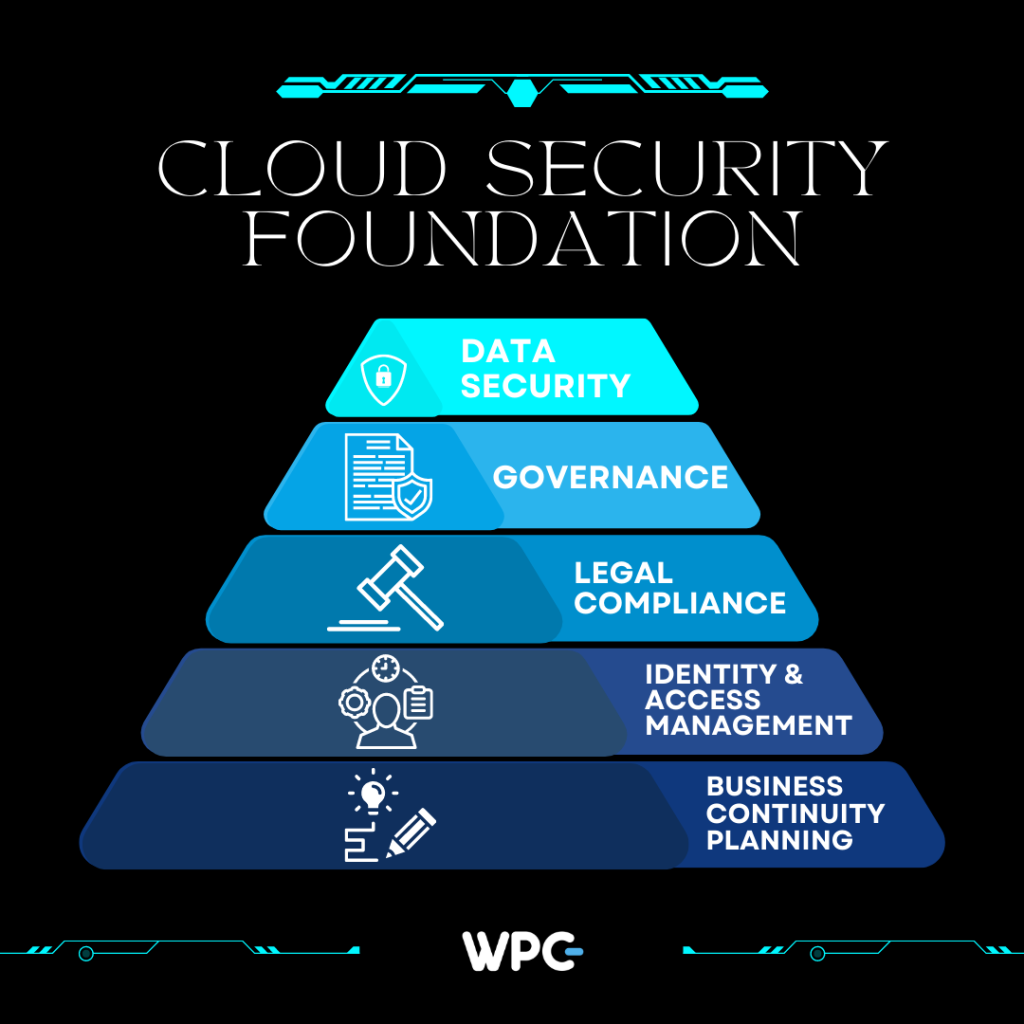
All You Need To Know About Cloud Security
A branch of cyber security called “cloud security” is devoted to protecting cloud computing...
Protect Your Heart: Valentines Day Cybersecurity
Valentine’s Day is known as the day of roses, hearts, lovebirds – and viruses. Cybercriminals...
Free Antivirus: The Bare Minimum
An antivirus tool is essential for protecting your computer from internet dangers including...
Invest in Technology: Grow Your Business Through Digital Transformation
In today’s economy, small businesses are more successful when they prioritize digital...
Our Accreditations