Small and medium-sized businesses (SMEs) are regarded as the foundation of the European economy. Over 100 million people are employed by the 25 million SMEs that operate in the EU. Due to the COVID pandemic and existing crisis, traditional businesses were forced to use previously unexplored technology like QR codes and contactless payments. Despite relying on such cutting-edge technologies, SMEs frequently failed to boost their security with respect to these new systems.rper mattis, pulvinar dapibus leo.
CAN SMEs BE TARGETS OF CYBERATTACKS?
Threats to cyber security can affect both large and small businesses. A prevalent fallacy for small businesses is the notion of security via obscurity, or that your company is too small to be a target. Sadly, this is untrue.
Attackers can target hundreds or even thousands of small businesses at once as attacks become more automated. Small organizations frequently have weaker technological defenses, less awareness of dangers, and fewer resources to devote to cybersecurity. Because of this, hackers may target them more easily than larger companies.
Due to these factors, small firms must be aware of the dangers and understand how to counter them. This article will cover the top 5 security dangers facing businesses, the risks, and impacts of an attack, and how businesses can protect themselves against them.
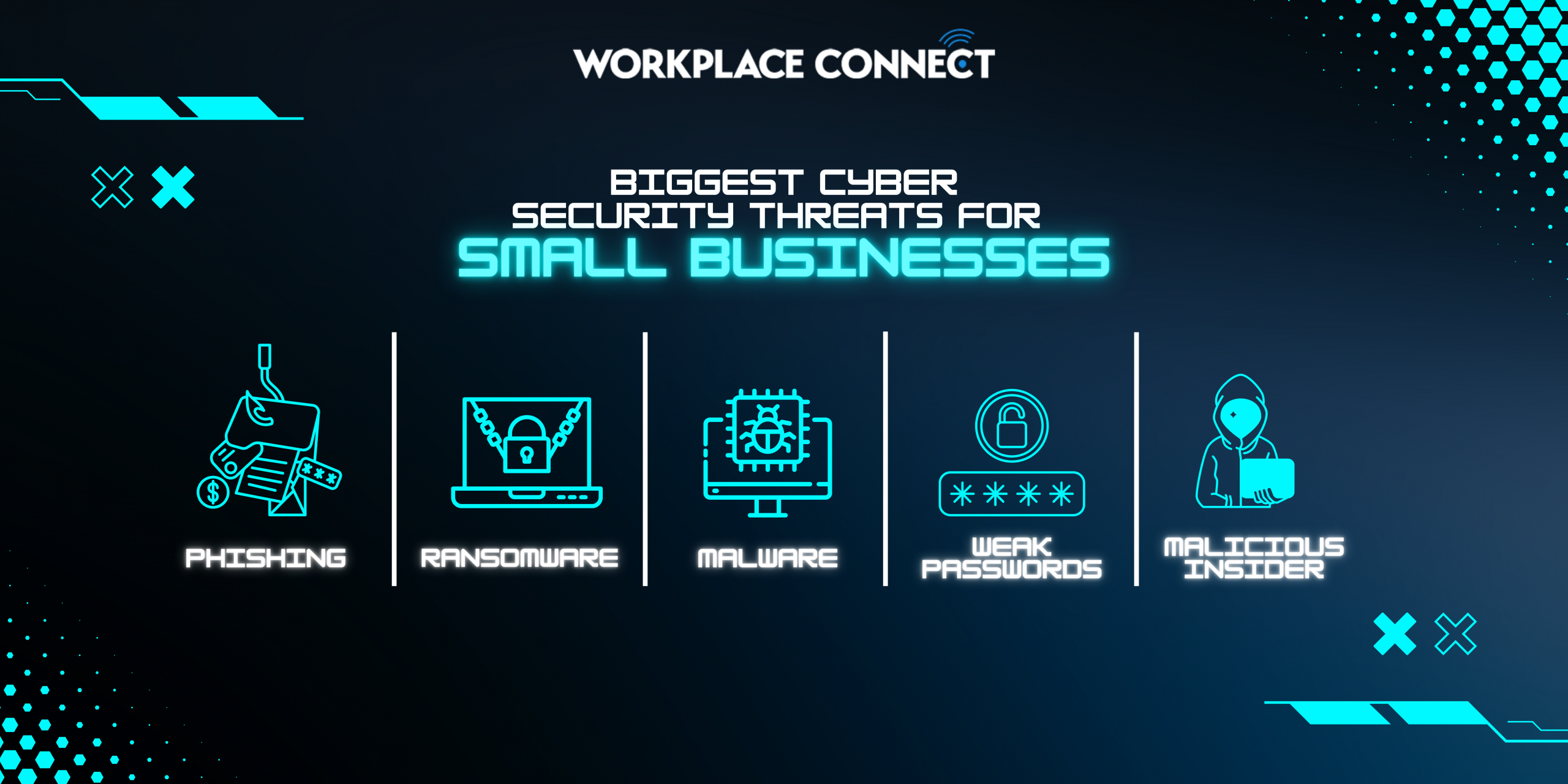
5 BIGGEST CYBERSECURITY THREATS FOR SMEs
1. Phishing Attacks
Phishing attacks are the biggest, most dangerous, and most pervasive threat to small businesses. 90% of breaches that affect enterprises are caused by phishing, which has increased 65% in the past year and cost companies over $12 billion in revenue. Phishing attacks happen when a perpetrator poses as a reliable source and persuades a victim to open a malicious file, click a malicious link, or provide sensitive data, account information, or login credentials.
Phishing assaults are particularly destructive since they are incredibly challenging to stop. Instead of focusing on technology flaws, they utilize social engineering to attack the people inside a company.
2. Ransomware
One of the most frequent cyberattacks, ransomware affects thousands of organizations annually. Due to the fact that these attacks are among the most lucrative types of attacks, they have only grown in frequency. Ransomware encrypts corporate data so that it cannot be used or accessed, and then demands a ransom payment from the firm in order to decrypt the data. Businesses are therefore faced with a difficult decision: pay the ransom and risk losing potentially enormous quantities of money, or risk having their services compromised by losing data.
Small firms are particularly vulnerable to this kind of attack. According to reports, small firms are the target of 71% of ransomware attacks, with an average ransom demand of $116,000. Because their data is frequently not backed up and they need to be fully operational as quickly as possible, attackers are aware that smaller companies are considerably more inclined to pay a ransom.
3. Malware
The next major hazard to small companies is malware. It includes a range of online dangers like viruses and trojans. Malicious code that hackers write to break into networks steal information, or corrupt computer data is referred to as malware. Malware typically originates via connections to other infected computers or devices, spam emails, or malicious website downloads.
These attacks can cripple electronics, necessitating costly repairs or replacements, which is especially harmful to small companies. They may also provide hackers with a back door to data, putting clients and staff in danger. Due to the time and cost savings, small businesses are more inclined to hire workers who bring their own devices to work. However, as personal devices are considerably more likely to be at risk from fraudulent downloads, this raises the possibility that they may be the victim of a malware attack.
4. Weak passwords
Employees who use weak or obvious passwords pose a serious threat to small companies. Numerous small businesses utilize multiple cloud-based services, each of which calls for a different account. Financial details and sensitive data are frequently present in these services. This information may be hacked if weak passwords are used, or if the same password is used across several accounts.
Employees who use weak passwords frequently put small organizations at risk for hacks since they are generally unaware of the harm they can do. 19% of industry professionals on average share passwords between accounts or use passwords that are simple to guess.
5. Malicious insider
The insider threat is the last great danger facing small firms. An insider threat is a danger that a company faces as a result of the behavior of current or former workers, business partners, contractors, or acquaintances. These individuals have access to vital information about your business, and they have the potential to cause harm out of avarice, malice, or even just negligence. According to a study by Verizon, insider threats were to blame for 25% of data breaches.
This is a problem that is becoming worse and could endanger consumers and staff or hurt the business financially. Insider risks are increasing in small firms as more employees have access to several accounts that contain more data.
What’s at Risk?
Your money, data, and IT equipment are all at risk from cyberattacks. The damage that a hacker could cause if they obtain access to your network includes:
- Accessing client lists
- Credit card details
- Details of your company’s banking
- Your pricing policy
- Product concepts
- Development plans
- Production procedures
These assaults endanger more than just your business. Hackers could enter the networks of other businesses whose supply chains you are a part of by using your network as a stepping stone.
What’s the Impact of an Attack?
A cyberattack may severely impact your company. In fact, 60% of small businesses that are attacked and suffer a breach close their doors within six months. There are still other repercussions that your company might endure, such as the following:
- Financial losses brought on by the theft of financial data
- Financial losses due to business disruption
- High expenditures to remove threats from your network
- Reputational damage after informing clients that their data had been compromised
How to address cybersecurity challenges?
People – In the cybersecurity ecosystem, people are crucial. In relation to confidential and/or sensitive information, the research emphasizes the value of accountability, employee buy-in, and awareness, cybersecurity training and policies, as well as third-party management.
Processes – Performing audits, incident prevention, and response, password monitoring, software patching, and data protection are all part of keeping an eye on internal company processes.
Technical – A number of factors related to network security, anti-virus, encryption, security management, data security, and the security of backups should be taken into account at the technical level.
While most SMEs lack the budget to “throw money at the problem” and spend whatever it takes to maintain strong security, these organizations can do more with less by harnessing the power of automation and continuous testing. Workplace Connect’s solution is our Standard and Managed Security Services — and the best tool SMEs have against today’s attackers.
Why Managed Security Service Is the Key to Proactive Cyber Defense
Our Standard Managed Security Service includes aspects like ensuring there are mail flow rules, enabling MFA and getting Endpoint Detection + Response anti-virus on the computer. This is a more generalized approach to security, which is a wise decision for companies lacking in these areas but are very cost-conscious. This would be a good foundation for your cyber security needs and is in line with cyber essentials to get certified
On the other hand, our Advanced Managed Security Service package includes DNS filtering for protecting against malicious websites, mobile device management, conditional access, and compliance profiles. The controls over the organization are more granular in order to address further potential security concerns – it brings in more control over the tenant and the devices, stopping potential attacks. It blocks sign-ins from risky countries and only allows access if the device meets the company’s security policies. Blocking sign-ins to personal devices to prevent data leakage. This package leans more toward businesses keen on ensuring compliance – legal or financial.